Managing information technology risk
Information technology (IT) has become an essential part of business operations by streamlining systems and reducing paperwork.
As many businesses now rely so heavily on IT, there are risks to consider should something go wrong.
Defining IT risk
If you own or manage a business that uses IT, it's important to identify risks to your IT systems and data so that you can reduce or manage those risks, and to develop a response plan in the event of an IT crisis.
Business owners have legal obligations in relation to privacy, electronic transactions, and staff training that influence IT risk management strategies.
IT risks include hardware and software failure, human error, spam, viruses and malicious attacks, as well as natural disasters such as fires, cyclones or floods.
By looking at how your business uses IT, you can:
- understand and identify the types of IT risks
- understand the impact of risks on your business
- manage risks using policies and procedures
- conduct regular staff training to further lower risk from potential threats.
Developing a risk management plan will help you to identify areas of potential risk in your business continuity plan.
Download the business continuity plan template
This template includes these 3 sections:
- risk management plan
- business impact analysis
- incident response plan.
Use this page to consider your IT risk, then complete the 3 sections of the template.
Download the business continuity planning template.
Identifying IT use within the business
Consider how IT is used within your business.
-
Do you do any of the following?
- Receive payments
- Pay creditors
- Move money between accounts
-
Do you manage business taxation? For example:
- Pay As You Go (PAYG)
- BAS reporting online.
-
myID connects with a broad range of business services, including:
- Australian Business Register (ABR)
- Australian Business Registry Services (ABRS)
- Austrade account portal
- Apprenticeships Data Management System (ADMS)
- Business Registration Service
- Export Market Development Grant application
- Online services for business—a system to report and manage tax and superannuation
- Research and Development (R&D) Tax Incentive customer portal
- Workforce Australia Online for Businesses—a free online recruitment service.
-
Do you use any of the following?
- File hosting and sharing services
- Websites
-
Do you use online stores to:
- sell goods and services
- purchase stock or business items.
-
Do you use software that is:
- pay by the month
- downloaded onto a personal computer (PC) or device
- accessed through a web portal or app.
Software examples are:
- financial software
- customer relationship databases (CRM)
- project management
- team collaboration software
- secure contracts, including signatures
- word processing
- spreadsheets
- databases
- presentations.
-
Do you use social media sites for:
- marketing
- customer communication?
-
Do you use a point-of-sale system to receive payments from customers?
-
Is your telephone system connected via the internet?
-
Do you have a non-mobile connection to the internet for email and internet activities?
-
Do you use a mobile phone for communication, email, photographs, or apps for the business?
-
Do you use a computer for broad range of business operations such as administration or graphic design?
Identifying types of IT risk
Using IT helps can help you to complete tasks faster and more efficiently. However, it can also introduce the risk of a serious IT failure that may result in your business needing to cease trading.
Identifying types of risk will help you complete your business continuity plan.
Case study: Point of sale systems
Cash transactions are becoming less common than in the past. Today, customers may not carry any cash into a retail environment, and this change in behaviour can cause a trading risk for a business.
An internet outage may impact the point of sale (POS) facilities, meaning customers can't pay for their purchase. There are also fewer cash outlets, such as ATMs, available to withdraw cash.
Make sure you have a plan in place to prepare for IT outages to avoid financial and other risks in your business.
General IT threats
These IT risks could impact your business:
- hardware and software failures—you may need IT expert assistance or to purchase a new computer to continue business operations
- malware—malicious software designed to disrupt computer operation
- viruses—codes that can spread from 1 computer to another, disrupting computer operations (e.g. sent through emails)
- spam, scams, and phishing—unsolicited contact that fool people into giving personal details or buying fake goods
- human error—accidentally opening an email containing viruses, incorrect data processing, or careless data disposal
- natural disasters—floods, storms, and bush fires may interrupt service within the business or to external suppliers (e.g. NBN, electricity).
Case study: VoIP phone service
A small business changed its telephone system to use the internet for telephone calls using VoIP (Voice over Internet Protocol).
The VOIP provider experienced flooding and their servers and network were not operational for several days.
No customers were able to contact the business on the VoIP telephones which resulted in several days of lost trade.
Read more about IT threat preparation for small business.
Criminal IT threats
Specific or targeted criminal threats to IT systems and data include:
- ransomware—software that prevents the user from accessing their files or any part of the computer system until a ransom is paid
- hackers—people who illegally break into computer systems
- fraud—using a computer to alter data for illegal benefit
- password theft—stealing log-in credentials to impersonate you for illegal gain
- denial-of-service—online attacks that prevent website access for authorised users
- security breaches—physical break-ins as well as online intrusion
- staff dishonesty—theft of data or sensitive information, such as customer details.
Case study: Payment fraud
Payment fraud is when cybercriminals steal business credentials and trick creditors into misdirecting their bill payments.
The owner of a building business sent an invoice to a customer for payment. Cybercriminals gained access to the builder's emails and were able to change the invoice details to another bank account.
The customer received what appeared to be a normal email from the builder with the invoice attached and therefore paid the bill however the payment went into the criminal's account.
It was only when the builder rang the customer asking why they had not paid that the crime was revealed.
Read more about:
Worst-case scenarios
To help identify risks and worst-case scenarios, ask 'what if?' questions with your staff, business mentor, or advisers.
What if:
- you lost power supply?
- you had no access to the internet?
- key financial documents were destroyed?
- your premises was damaged, and you were unable to gain access?
- one of your staff with extensive IT knowledge left the business?
- staff brought their own devices to work, downloaded company software and accessed sensitive work data on the device?
- staff did not know about cyber security and how to prevent malware and phishing?
- staff had access to your electronic banking login?
- staff shared passwords?
- you don't have two-factor authentication on your business software?
Managing IT risk with policies and procedures
The Prevention, Preparedness, Response, Recovery (PPRR) risk management model identifies risks to include in your business's policies and procedures.
By preparing policies and procedures that all staff can follow, you can reduce or prevent IT risk.
Policies and procedures to protect your business from risk
| Policy | Procedures within policy |
|---|---|
| Policy for use of software |
|
| Bring your own device policy |
|
| Information Technology security policy |
|
| Electronic transactions policy |
|
| Emergency management of Information Technology |
|
Managing IT risk with practical steps
There are practical steps you can take to improve IT security within your business.
These include:
- securing computers, servers, and wireless networks
- using anti-virus and anti-spyware protection, and firewalls
- updating software to the latest versions
- using data backups that include off-site or remote storage
- securing your passwords
- implementing two-factor authentication
- training staff in IT policies and procedures
- using Secure Socket Layer (SSL) on websites
- understand legal obligations for online business.
Read more about cyber security and protecting your online business activity.
Legal obligations for online business
As a business owner there are legal and legislative requirements to be aware of when it comes to IT operations.
These include:
Read more about meeting your legal obligations.
Action item
Consider how the policies, procedures and practical steps outlined here could help you prevent or reduce IT risks in your business.
Use your business continuity planning template to record these policies and procedures in your risk management plan in the Preventive actions and Contingency plans columns.
Also consider what to do in the event of an IT incident and record this in these 2 sections:
- incident response
- recovery.
Insuring your business against IT risk
It can be very difficult to avoid all IT incidents. Business insurance may provide another way to reduce risk.
Find out more about business insurance.
Training your staff
Staff can be the first and last line of defence against IT threats so investing the time for initial and ongoing training is a good preventative measure to avoid risks occurring.
Consider:
- conducting cyber security training when new staff members start with the business
- updating staff and training manuals when
- new risks or threats are introduced
- changes have occurred to risks
- sharing examples of frauds so staff can better identify them
- creating a strong cyber security culture among staff.
Use these free staff training resources from the Australian Cyber Security Centre.
- Learn how to spot scam phishing scams.
- Use the First Nations Business Resources.
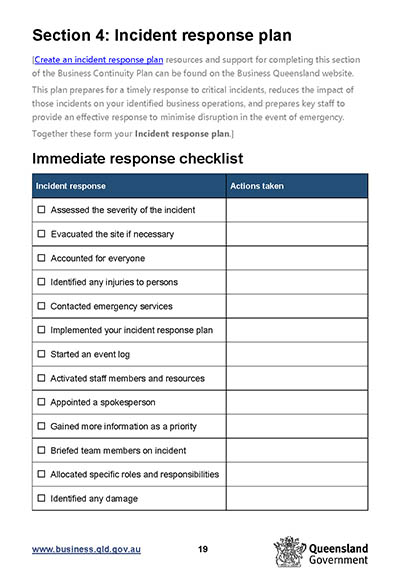
Responding to an incident and recovery planning
IT incidents may be the result of a wider crisis, such as an explosion, bushfire, or flood. In any emergency situation, the safety of staff and members of the public are your first priority. An IT incident response plan should support any emergency response plan you have developed.
If an IT incident or crisis occurs, having a recovery plan in place will assist in reducing the business's recovery time and help to minimise losses.
A plan could include:
- strategies for the business to begin operating in the quickest possible time
- a list of key resources and equipment required to return to operations
- your recovery time objectives.
Read more about developing a recovery plan.
Also consider...
- Learn how to manage risk with business insurance.
- Find out how to write a business continuity plan.
- Explore managing risks when starting up.
- Watch our Cyber security for small business webinar for information, tips and resources on protecting yourself and your business from cyber security threats.
- Learn more about cybersecurity for business from our Mentoring for Growth mentors.